
When RedLens InfoSec, a division of CampusGuard, performs penetration tests, it doesn’t just look for known vulnerabilities—it’s also on the lookout for zero-day vulnerabilities. When a zero-day vulnerability is discovered, we work with the vendors on behalf of our customers so that patches can be created to further protect these systems. In the process, we coordinate with MITRE, a not-for-profit private company that created and manages the CVE program, for the betterment of all users of a particular system/software product
The CVE program (Common Vulnerabilities and Exposures) is a publicly available dictionary of unique identifiers for publicly known cybersecurity vulnerabilities and exposures. The program was created to standardize the naming of vulnerabilities and to facilitate the sharing of data between different organizations, researchers, and vendors.
The goal of the CVE program is to help ensure that cybersecurity vulnerabilities are disclosed, identified, and addressed in a timely and effective manner. The program allows organizations and individuals to easily track vulnerabilities across different systems and software, and to quickly identify which systems may be affected by a particular vulnerability. This enables better prioritization of security efforts and facilitates the development of patches and other mitigations.
Identifying CVEs allows researchers to contribute to the broader cybersecurity community by providing information about new vulnerabilities that can be used to improve security across all organizations, and plays a crucial role in improving the security of the digital ecosystem.
Here is an example of one recent discovery while completing a pen test.
CVE-2022-37462 – Upstream Chat Gadget Stored Cross-Site Scripting
Introduction:
Upstream Works for Finesse, an omnichannel contact center software that offers real-time communication between customers and support agents, has a vulnerability in its chat gadget that can be exploited by attackers to execute malicious JavaScript in the support agent’s browser. The flaw affects Upstream Works for Finesse software from the 4.x branch prior to 4.2.14 and software from the 5.x branch prior to 5.3. A stored cross-site scripting (XSS) vulnerability makes it possible for the attacker to attempt to gain credentials, deface the support agent console, or cause a denial-of-service condition.
Recommendation:
Update Upstream Works for Finesse versions 4.x to Engineering Release 4.2.14
Update Upstream Works for Finesse versions 5.x to Engineering Release 5.3
Impact:
Malicious JavaScript uploaded by an attacker will be executed in the support agent’s browser. The executed payload can be used to attempt to gain credentials, potentially execute functions masquerading as the support agent, deface the support agent console or cause a limited denial-of-service condition, or other malicious actions.
Stored XSS vulnerabilities are particularly dangerous because they execute automatically whenever a suitable victim accesses the resource. Victims will not be forewarned by suspicious activity from an unknown party, and the payload will only execute when an authenticated user has navigated to the desired location. This allows the attacker to produce highly targeted exploits, as the attacker knows the exact programmatic context of a victim when the code executes.
Details:
Chat programs are used extensively by companies to provide real-time support to customers. Because Hypertext Transfer Protocol (HTTP) is a synchronous protocol, almost all of these programs use WebSockets, a computer communications protocol providing full-duplex communication channels over a single transmission control protocol (TCP) connection, to support asynchronous communications.
Like most modern chat programs, the UpstreamWorks chat gadget allows clients to upload files to share with support agents:
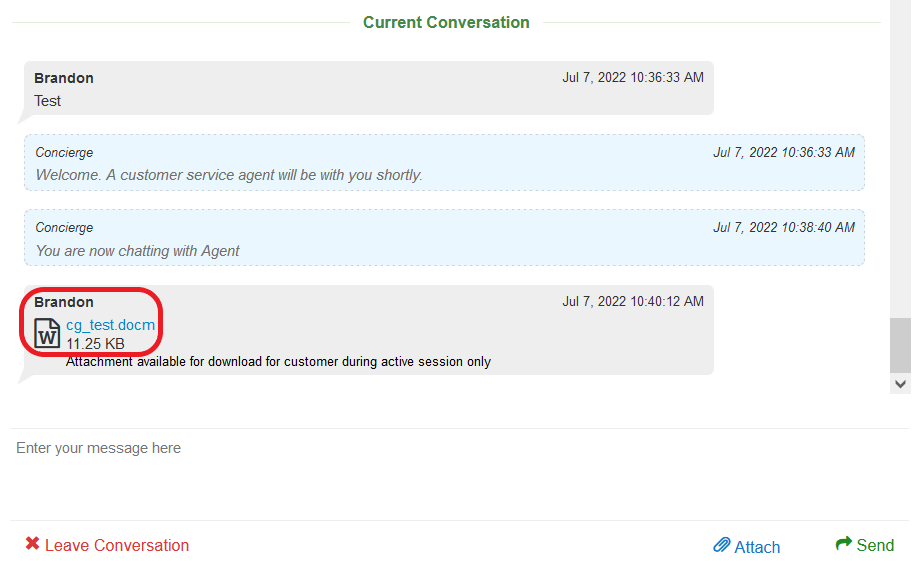
Figure 1 – File Upload via Chat Gadget – Client View
The chat program transmits the file contents via an HTTP request. However, file details that will be integrated into the current conversation with the support agent are transmitted via the established WebSocket connection. In order to insert the malicious payload, we intercept and manipulate the data transferred via the WebSocket connection. We have to ensure the payload is properly escaped for the JSON parser:
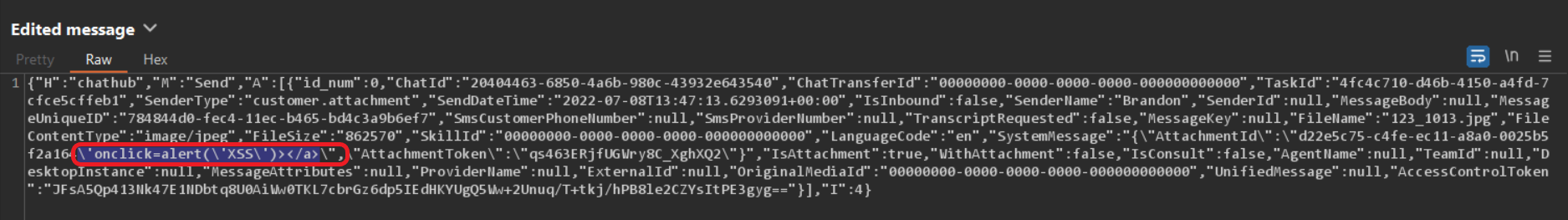
Figure 2 – XSS Payload
A vulnerable function in agent.js uses inadequately sanitized client-supplied data to craft the download link for the support agent when the customer uploads a file:
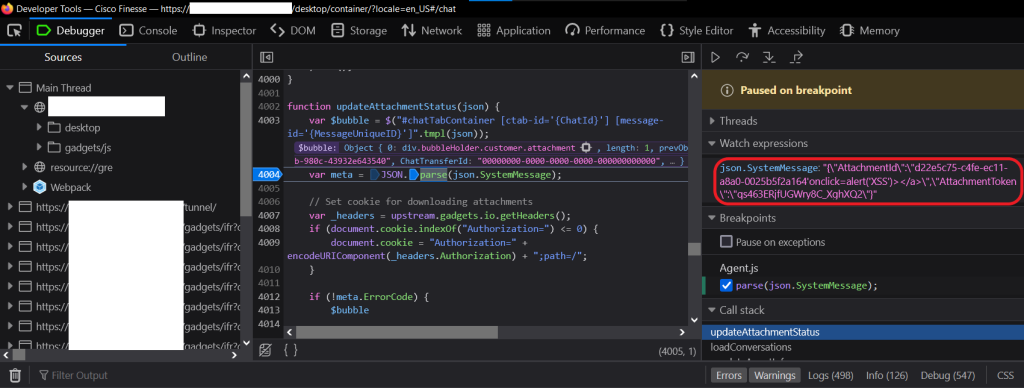
Figure 3 – Vulnerable Function
The proof of concept payload displays a simple prompt using the alert() function:
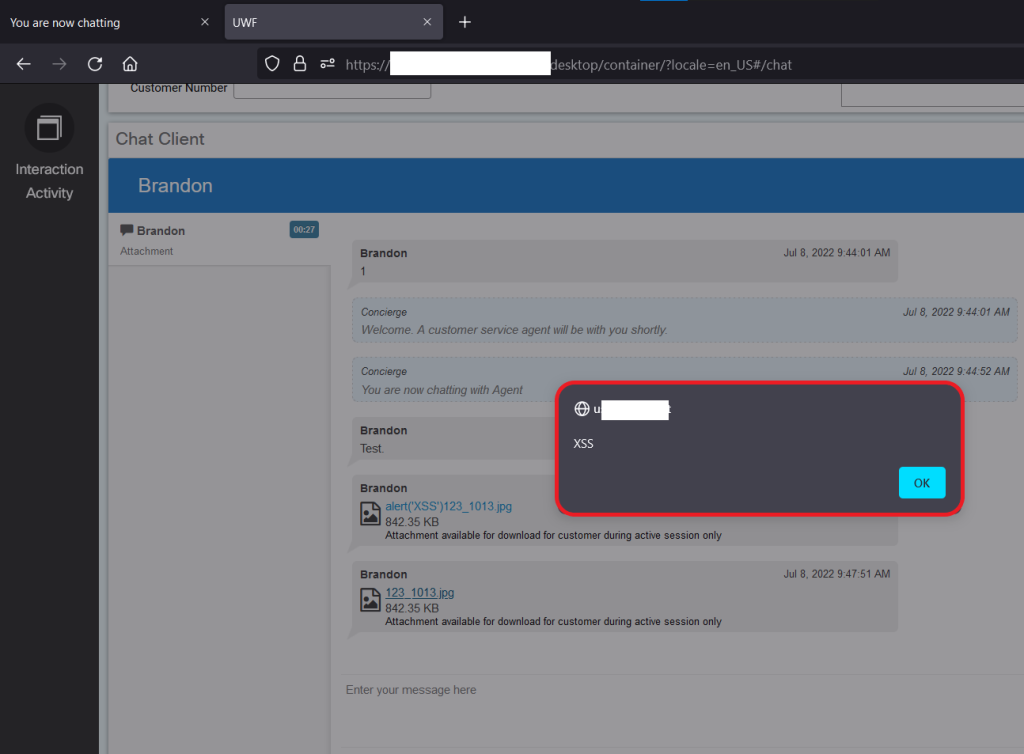
Figure 4 – XSS Prompt
RedLens InfoSec delivers comprehensive pen testing by evaluating and offering recommendations to improve your organization’s security posture, testing its existing defense capabilities, limiting the damage of a possible security attack, and assisting in executing legal or regulatory compliance requirements. Contact us to learn more.

